Device Images (NOS)¶
The Device Images section acts as the secure repository for Network Operating System (NOS) binaries.
This library centralizes the firmware files used for upgrade operations (ZTP or Day-2 maintenance). By decoupling the image from the specific device model and linking it to the Device Family, Avalon simplifies fleet-wide compliance.
Uploading a New Image¶
To add a firmware file to the repository, use the upload form at the top of the page.
Warning: Do not leave the page during upload
Uploading an image may take several minutes depending on the file size. Do not close the page or navigate away during the process, or the upload will be interrupted and must be restarted.
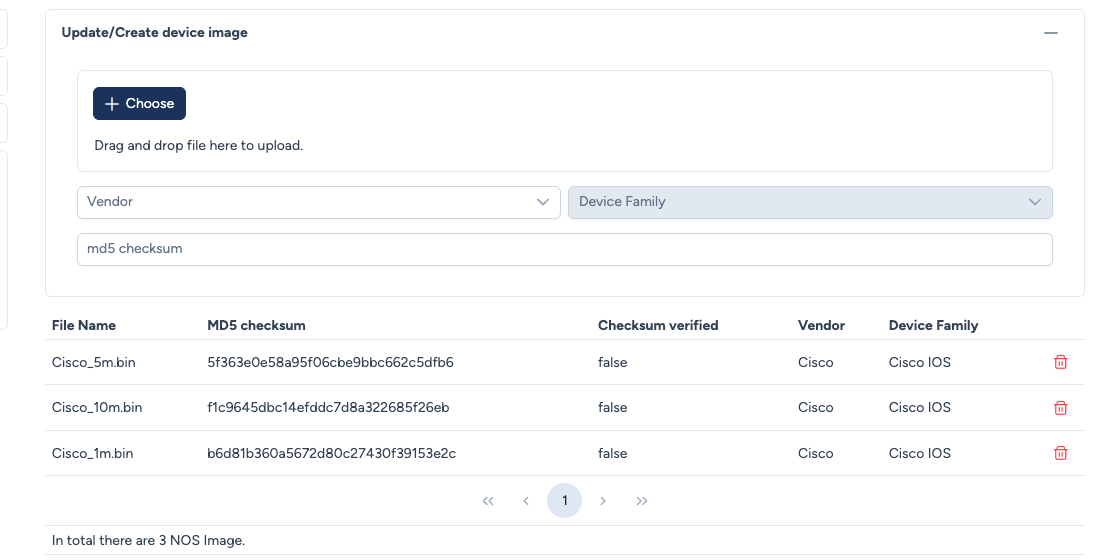
Configuration parameters:
- File Selection: Drag and drop the
.bin,.iso, or.qcow2file from your local computer. - Vendor & Device Family: Defines the scope of the image.
- Rule: Once uploaded, this image becomes eligible for any device model belonging to the selected Family.
- MD5 Checksum (Optional but Recommended): You can manually paste the official hash provided by the vendor (e.g., from the Cisco Software Download page).
Integrity verification (MD5)¶
Avalon implements a rigorous "End-to-End" integrity check to prevent corrupted deployments.
1. Upload Verification (Repository Level) When the file is uploaded, Avalon calculates its MD5 hash on the server side.
- If you provided a checksum: Avalon compares the calculated hash with your input. If they match, the
Checksum verifiedstatus becomes True. - If you left it blank: Avalon stores the calculated hash but flags the verification as False (since no external source confirmed it).
2. Transfer Verification (Device Level) During an upgrade workflow, Avalon uses the stored hash to verify the file integrity again after transferring it to the physical equipment (via TFTP/SCP) but before booting it.